Prevent Overlayfs Privilege Escalation on Ubuntu Kernels with Yaml (bpf)
Learn about the overlayfs upstream vulnerability in the kernel and how to prevent the escalation of the vulnerability using Tetragon
Learn about the overlayfs upstream vulnerability in the kernel and how to prevent the escalation of the vulnerability using Tetragon
Delve into how Cilium can be used alongside the security groups for EKS pods in supported clusters when running in chaining mode
Learn how the AKS-managed kube-proxy DaemonSet can be disabled to support BYOCNI (Bring your own CNI) and install Cilium as the CNI
Dive into an interview with Roland Wolters, Head of Technical Marketing at Isovalent, to find out more about the new Cilium 1.14 release and the community
Learn how to configure Cilium to supply Load Balancer service support in Kubernetes
Learn about some of the most exciting features in the Cilium 1.14 release
Explore the reasons why Trendyol chose Cilium and the value they received from it
Learn how to install a Kubernetes 1.27 Cluster, with 3 workers and 1 master nodes, on Ubuntu with Kubeadm and Cilium as CNI
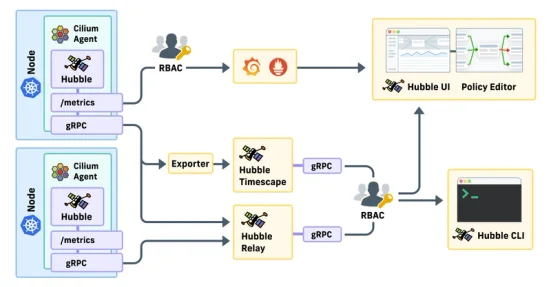
Explore some of the scenarios and integrations with other systems that enterprise users of Hubble might encounter and how Isovalent Cilium for Enterprise addresses them
For live conversation and quick questions, join the Cilium Slack workspace. Don’t forget to say hi!
Join slack workspace